The computer system structure consists of interrupt mechanism for I/O devices, memory unit to run programs, memory protection, and disk storage to save program and data files.
Computer-system operations
A modern general purpose computer has CPU and device controllers for devices such as disk, audio devices, and video display devices connected to a common system bus. Each controller is for a specific device only and it has a local buffer.
The CPU and device controllers can run concurrently and compete for memory. A memory controller synchronizes access to shared memory.
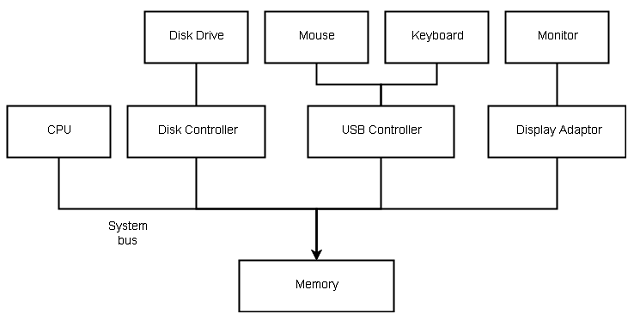
When a computer starts it initiates a simple program called the bootstrap program stored in a read-only memory (ROM) or erasable programmable read-only memory (EPROM). The bootstrap is a simple program that initiates the system and loads the OS in memory. The OS waits for an event called.Interrupt
There are two types of interrupts – hardware and software interrupt. The hardware generates interrupt by signaling the CPU directly. A software interrupt is performed by a system call also known as monitor call. The CPU stops current operation and transfer the control to a fixed memory location where interrupt service routine (ISR) for the interrupt is located. Once interrupt service routine finished execution, the CPU resume the control of the interrupted operation.
Two things are very important, no matter how OS is designed:
- CPU must efficiently transfer the control to ISR.
- Speed up the process of transfer.
The ISR can call an interrupt handler to check the appropriate handler, but it is not necessary because there are few fixed addresses for ISRs. Hence, a table of pointers to the ISR address called isInterrupt vector maintained. The indexed interrupt vector immediately transfers the control to the correct ISR of a device upon receiving interrupt request.
The interrupt mechanism must save the address of the interrupted instruction in a fixed memory location, or a stack and load this address to program counter once the interrupt routine is completed. This will appear as if the interrupt never happened.
Computer Storage Structure
The computer storage consists of two main memory – primary memory or main memory and secondary memory/disk drives. The program is loaded into a rewritable main memory called RAM (random access memory). The memory is organized using words where each word has its own memory address
A computer based on Von Neumann architecture reads an instruction in CPU registers and decode the instruction and fetch the required operands from memory and store the result back to the main memory. The main memory and registers are primary storage because the CPU can access them directly if they are not accessible, then it must be brought to the memory before the CPU can manipulate them.
There are two concerns while CPU access the memory addresses:
- Speed of memory access
- Memory access protection
The CPU is very quick in fetching and decoding the instructions, but of the operands are not in registers, the memory fetch could delay the CPU operations. Cache memory is faster memory that can speed up the memory access.
Secondly, each program must use its own memory space, otherwise, it would be illegal access and result in a program crash. To protect memory we use two registers – base register and limit register.
The base register contains the starting memory address of a process and limits register contains the size of the range of addresses for the process. See the figure below.
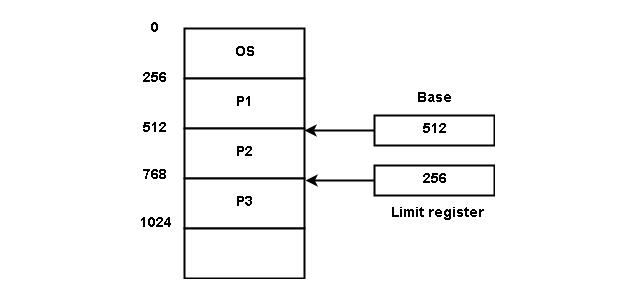
For example, base register = 512 and limit register = 256
Then the process P2 in the above figure can only access all addresses from 512 to (512 + 256) = 768. If the program tries to access any other address outside this range, an interrupt happens.
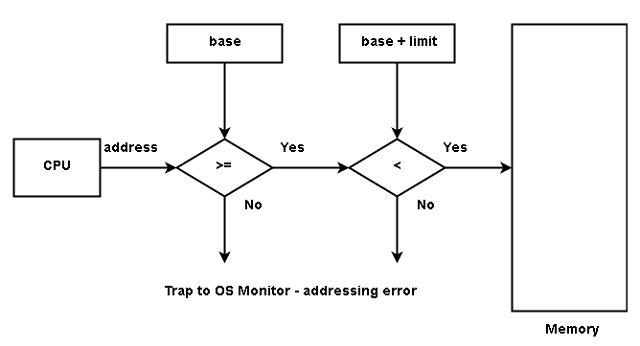
Therefore,
\begin{aligned}
Legal \hspace{1ex}address >= Base \hspace{1ex}register \hspace{1ex}value\\ \hspace{1ex}AND < (Base\hspace{1ex} register\hspace{1ex} value + Limit \hspace{1ex}register \hspace{1ex}value)\end{aligned}Any address generated by user application is verified by CPU hardware with the registers if the user application tries to access operating system memory address the OS trap is generated. The OS loads the base register and limit register and has the ability to modify the address because OS runs in kernel mode. The application which runs in user mode cannot access the registers. You will learn about user mode and kernel mode in the next article.
Logical address and Physical address
A logical address is also called a virtual address because it is user generated. The virtual address is mapped to a physical address which is the real memory address with the help of base and limit registers.
For example, suppose
\begin{aligned}
&Base = 3000\\
&Limit = 1500\\
&Legal address >= 3000 < 4500
\end{aligned}If the virtual address is ![]() , then the OS generates a physical address of
, then the OS generates a physical address of ![]() . This address is within the limit of
. This address is within the limit of ![]() .
.
The memory space is very less and only include programs that are running. What about the programs that are not executing currently? Where do we store them? Such programs are in the form of files and stored in secondary storage devices called tape or disk drives.
Disk Storage Structure
Magnetic tape or disk is called a secondary storage device. It has huge space compared to the main memory space. The disk storage device comes in various sizes, sometimes more than 1 terra bytes disk is used in computer systems.
Though the magnetic disks have large space when compared to main memory, the magnetic disks are slower to access. It takes more CPU time to perform an I/O operation than a CPU bound memory operation.
For this reason, the CPU remains idle most of the time in a single user system. In a multi-tasking system, the CPU can process another user. In the next article, you will learn about OS structure and how CPU performance is optimized in a time-sharing computer.
References
- Abraham Silberschatz, Peter B. Galvin, Greg Gagne (July 29, 2008) Operating SystemConcepts, 8 edition edn., : Wiley.
- Tanenbaum, Andrew S. (March 3, 2001) Modern Operating Systems, 2nd edn., Prentice Hall.
